Many experienced penetration testers will write a set of instructions that runs in sequence to perform tasks on a computer system. What type of resource are these penetration testers utilizing?
A. kiddies
B. packets
C. scripts
D. tasks
Answer: C
Computer Science & Information Technology
You might also like to view...
Which statement below initializes array items to contain 3 rows and 2 columns?
a. int[][] items = {{2, 4}, {6, 8}, {10, 12}}; b. int[][] items = {{2, 6, 10}, {4, 8, 12}}; c. int[][] items = {2, 4}, {6, 8}, {10, 12}; d. int[][] items = {2, 6, 10}, {4, 8, 12};
Computer Science & Information Technology
Many font options are located in the Font Dialog Box Launcher in the __________.
A. FONT tab B. Font group C. Font ribbon D. Font box
Computer Science & Information Technology
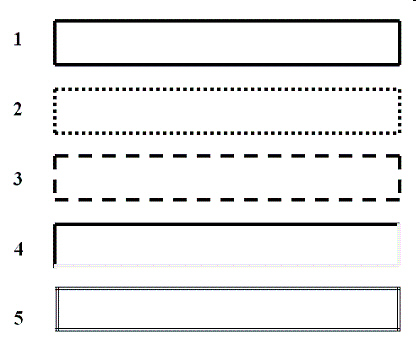 The item marked 5 in the accompanying figure is an example of the ____ style.
The item marked 5 in the accompanying figure is an example of the ____ style.
A. dotted B. double C. dashed D. inset
Computer Science & Information Technology
A slide's aspect ratio refers to the ________ of a screen
A) height-to-depth B) width-to-height-to-depth C) width-to-height D) width-to-depth
Computer Science & Information Technology