An advantage to brute-force password attacks is that they take little time to perform even as key lengths increase.
a. true
b. false
b. false
Computer Science & Information Technology
You might also like to view...
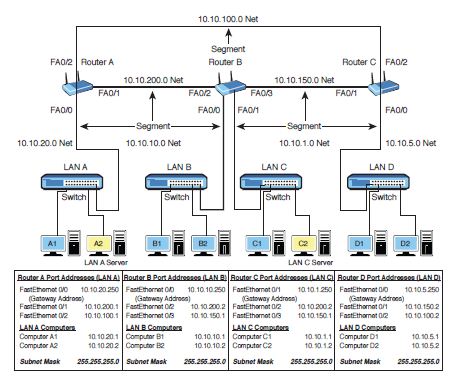
What is the next hop address for FastEthernet port 1 on Router A in Figure 8-12?
Figure 8-12
Computer Science & Information Technology
What is the first phase of the development of a security policy likely to involve?
A. remediation of employees that violate the policy B. review of the policy for compliance C. vulnerability assessment D. an outline of how the organization will respond to attacks
Computer Science & Information Technology
The ________ control is used to add an existing form to another form as a subform
Fill in the blank(s) with correct word
Computer Science & Information Technology
A red dot indicates the ending point of a motion path
Indicate whether the statement is true or false
Computer Science & Information Technology