If employee is an array of objects with a public member function named set Hours Worked, which of the following statements correctly calls that function for the employee object in array element 5?
A) employee. set Hours Worked[5] = 40;
B) employee[5].set Hours Worked = 40;
C) employee .set Hours Worked[5](40);
D) employee[5].set Hours Worked(40);
E) set Hours Worked(employee[5], 40);
D) employee[5].set Hours Worked(40);
You might also like to view...
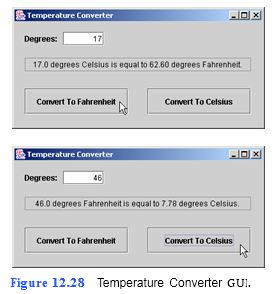
Write an application that performs two types of temperature conversions: degrees Fahrenheit to degrees Celsius and degrees Celsius to degrees Fahrenheit. Your output should look like Fig. 12.28.
a) Copying the template to your working directory. Copy the C:Examples Tutorial12ExercisesTemperatureConverter directory to your C:SimplyJava directory.
b) Opening the template file. Open the TemperatureConverter.java file in your text editor.
c) Adding a method to your application to convert from Celsius to Fahrenheit. On line
147, add a comment indicating that the method will convert the temperature from Celsius to Fahrenheit. On line 148, add the method header for this method. The method will be called convertToFahrenheit. This method returns a value of type double and takes an argument of type double. Name the double parameter degree. On line 149, add a left brace to begin the body of the method. On line 150, add a return statement that performs the conversion calculation. To do this, follow the return keyword with the following expression:
( 9.0 / 5.0 ) * degree + 32.0;
On line 152, add the right brace to end the body of the method. Follow
To protect WLAN traffic from eavesdroppers, a variety of security standards and practices have been developed, including all of the following except what?
A) Enabling SSID broadcast B) MAC address filtering C) Preshared key D) IEEE 802.1X
What is NOT one of the four main categories that are monitored by Resource Monitor?
A. CPU B. Memory C. Disk D. Firewall
Explain the benefits of logging in with your Microsoft account.
What will be an ideal response?