The information a function receives is listed in the ____ in the header.
A. parameterList
B. data type
C. return type
D. function name
Answer: A
You might also like to view...
The server name portion of a URL is also called the ____________________ name.
Fill in the blank(s) with the appropriate word(s).
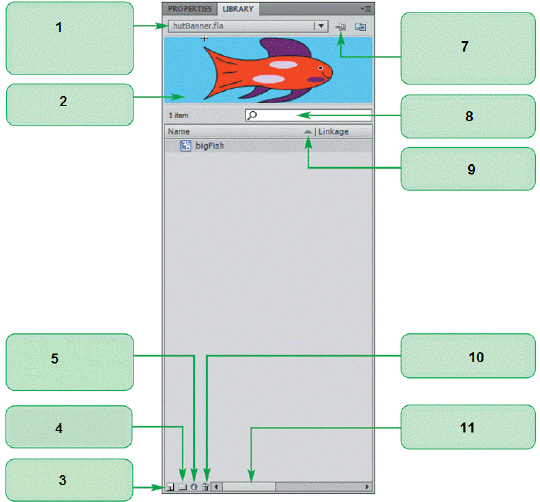 The item marked ____ in the accompanying figure is used to create a new symbol.
The item marked ____ in the accompanying figure is used to create a new symbol.
A. 2 B. 3 C. 4 D. 8
The animation technique made famous by Disney involves showing a different image for each frame. This technique is called ____________________ animation.
Fill in the blank(s) with the appropriate word(s).
A security administrator must implement a system to allow clients to securely negotiate encryption keys with the company's server over a public unencrypted communication channel. Which of the following implements the required secure key negotiation?
A. PBKDF2 B. Symmetric encryption C. Steganography D. ECDHE E. Diffie-Hellman