What are the main characteristics of Trinoo?
What will be an ideal response?
Trinoo is a distributed tool used to initialize coordinated UDP flood DoS attacks from multiple sources. A Trinoo network consists of a minute quantity of servers and a large number of clients. The two components are the Trinoo server and the Trinoo clients.?A hacker computer is connected to a Trinoo master computer in a DoS attack utilizing a Trinoo network. Then the hacker computer instructs the master computer to begin DoS attacks against one or more IP addresses. Next, the Trinoo master computer communicates with the Trinoo clients, giving them instructions to attack one or more IP addresses within a specified period of time.
You might also like to view...
adds two vectors Vect operator+( const Vect& vectA, const Vect& vectB )
What will be an ideal response?
FIGURE EX 5-1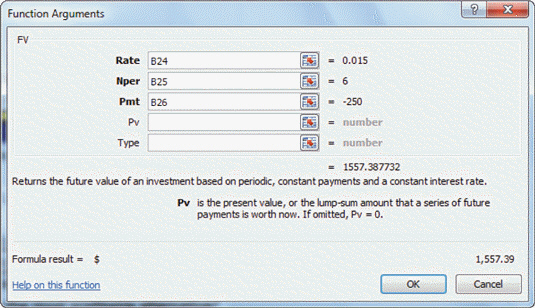 In Figure EX 5-1 above, the Pmt figure is -250. The negative number means ____.
In Figure EX 5-1 above, the Pmt figure is -250. The negative number means ____.
A. the entry is income B. the entry is a payment C. there is an error D. the person is behind on their payments
Which type of hackers break into systems for the thrill or to show off their skills.
A. Gray-hat B. White-hat C. Black-hat D. Blue-hat
Case Based Critical ThinkingCase 1Rae is building a website for the local chamber of commerce. This week, Rae is designing and completing a page that contains a list, headings, body text, images, and a background. During this process, Rae develops a style sheet for the project. To create an unordered list, what is the first step?
A. Click the Unordered List button. B. Select the text. C. Click the Style list arrow. D. Deselect the text.