ENIAC's memory held programs but not data.
Answer the following statement true (T) or false (F)
False
You might also like to view...
Which of the following is true about using inheritance in software engineering?
a. Common attributes and behaviors should be factored out of closely related classes and placed into a base class from which the original classes can now inherit. b. It is best to create a huge class library to make it easy for a client to find the most appropriate class for his or her needs. c. A class produced through inheritance should be as large as possible to fully encompass all of the functionality it should offer. d. The standard C++ libraries that are shipped with C++ compilers are usually enough to accomplish anything an application might need to do.
In Excel, B:G represents a range of ________
Fill in the blank(s) with correct word
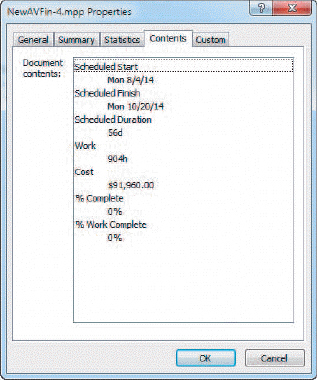 Which of the tabs in the accompanying figure allows you to find out when a project file was last modified?
Which of the tabs in the accompanying figure allows you to find out when a project file was last modified?
A. General B. Summary C. Custom D. Statistics
A Unicode input validation attack is an example of what type of attack?
a. Buffer overflow attack b. Source disclosure attack c. File system traversal attack d. Vulnerability attack