Which of the following enables the attacker to attack and debug web applications?
a. Cookies
b. URL obfuscation
c. Cross-site scripting
d. Web proxies
ANS: D
Computer Science & Information Technology
You might also like to view...
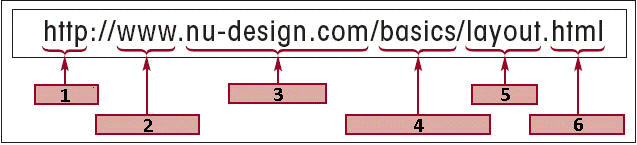 In the accompanying figure, the item marked ____ is the filename.
In the accompanying figure, the item marked ____ is the filename.
A. 3 B. 4 C. 5 D. 6
Computer Science & Information Technology
What type of bus does PCI Express use?
A. serial B. virtual C. parallel D. logical
Computer Science & Information Technology
Describe SSL VPNs, and compare the two most common types.
What will be an ideal response?
Computer Science & Information Technology
__________ addressing indicates that the value is encoded in the instruction.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology