A(n) ____ can cause a vast number of damaging actions ranging from profane messages to destruction of files.
A. spike
B. brown-out
C. UPS
D. virus
Answer: D
Computer Science & Information Technology
You might also like to view...
The role of the ____ function is to ensure that adequate preparation has been done to underwrite the success of the organization's response to an incident.
A. threat management B. risk management C. vulnerability management D. incident management
Computer Science & Information Technology
An async method executes its body in ________.
a) the calling method b) the called method c) the main method d) the same thread as the calling method
Computer Science & Information Technology
Which of the following would not be considered a constituent of a row group element?
A. table list B. table header C. table body D. table footer
Computer Science & Information Technology
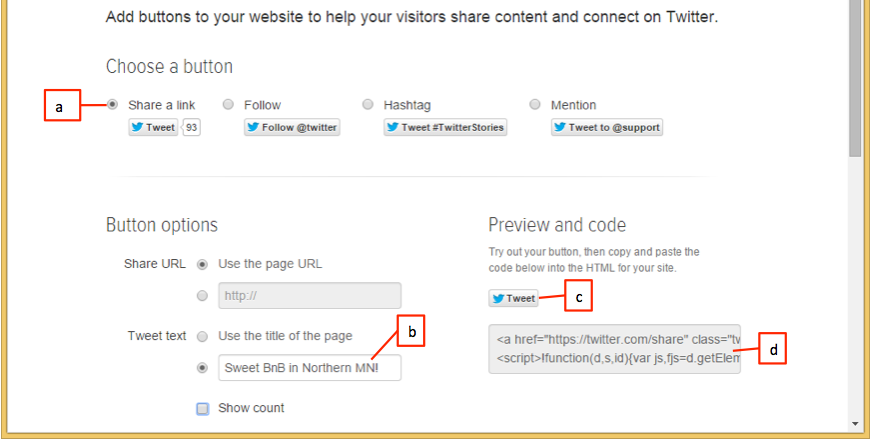
A. a B. b C. c D. d
Computer Science & Information Technology