Initial exchanges of public keys are vulnerable to the man-in-the-middle attack. Describe as many defences against it as you can.
What will be an ideal response?
1. Use a private channel for the delivery of initial keys, such as a CDROM delivered by hand or by some other rellable method.
2. Include the Domain Name in the certificate and deal only with the correct corresponding IP address.
3. If certificates are delivered through the network, validate them with a ‘key fingerprint’ – a character string that is derived from the key with a standard one-way function - that was delivered by a separate channel (e.g. on a business card).
You might also like to view...
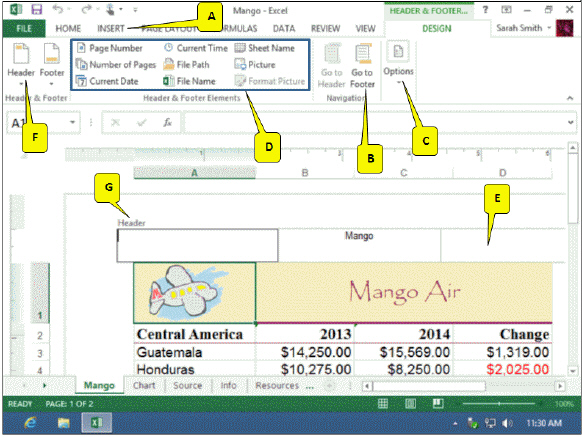 In the accompanying figure, which callout points to the button you should click to select header and footer options?
In the accompanying figure, which callout points to the button you should click to select header and footer options?
A. F B. C C. D D. B
When an element is stored in a map, it is stored as an object of the __________ type.
a. map b. key c. pair d. key_value e. None of these
COGNITIVE ASSESSMENT What does Microsoft produce and sell with computers and mobile devices?
A. software B. ?BIOS C. ?firmware D. code
Which of the following is a valid heading for a method that could accept the two-dimensional array as an argument?
A. void DisplayOutput(double [ , ] anArray) B. void DisplayOutput(double [10 , 2 ] anArray) C. void DisplayOutput(double anArray) D. void DisplayOutput(double anArray [10 , 2])