What is an application that entices individuals who are illegally perusing the internal areas of a network by providing simulated rich content areas while the software notifies the administrator of the intrusion?
A. port scanner
B. sacrificial host
C. honey pot
D. content filter
Answer: C
You might also like to view...
When there is a problem with a formula, a(n) ________ appears
A) null B) error message C) circular reference D) conditional format
Referring to the figure below, please identify the letter of the choice that best matches the numbered area on the screen.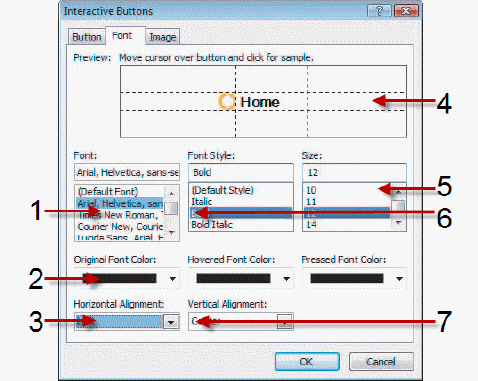
A. The area you would use to change the font to Camtasia. B. C. The area you would use to align the text to the right edge of the button. D. E. The area you would use to change the font size. F. The area you would use to make the text bold. G. The area you would use to align the text to the top edge of the button.
UDP is a connection-oriented protocol.
Answer the following statement true (T) or false (F)
Which of the following is a native Linux printer sharing protocol?
A. TCP B. SMB C. CUPS D. NFS