Which type of firewall keeps track of each network connection established between internal and external systems?
A. packet filtering
B. stateful packet inspection
C. application layer
D. cache server
Answer: B
You might also like to view...
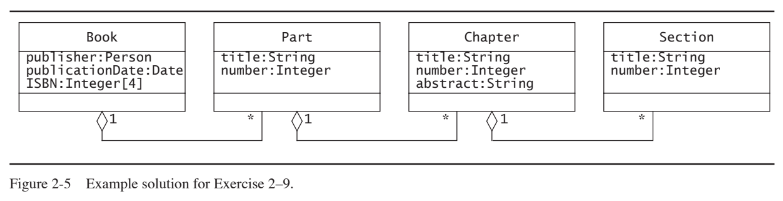
Consider the class diagram of Exercise 2–9. Note that the Part, Chapter, and Section classes all include a title and a number attribute. Add an abstract class and a generalization relationship to factor out these two attributes into the abstract class.
The library methods for both character-by-character and complete C-string input/output are contained in the ____ header file.
A. iostream B. iomanip C. cstdlib D. cctype
Which of the following may be used as a wildcard character when searching for a value in Access?
A. % B. # C. ^ D. &
if (maxValue = 100) System.out.println ("Your limit has been reached"); ? Why is the above if statement illegal? How would you fix it?
What will be an ideal response?