____ attacks often involve the act of obtaining passwords or specific pieces of information through iterative trial and error.
A. Conditional
B. Schematic
C. Brute force
D. Row set
Answer: C
Computer Science & Information Technology
You might also like to view...
What type of computer scientist studies how to make a computer think?
What will be an ideal response?
Computer Science & Information Technology
A _________ is the basic element of data.
A) ?database B) ?field ? C) ?file ? D) ?record
Computer Science & Information Technology
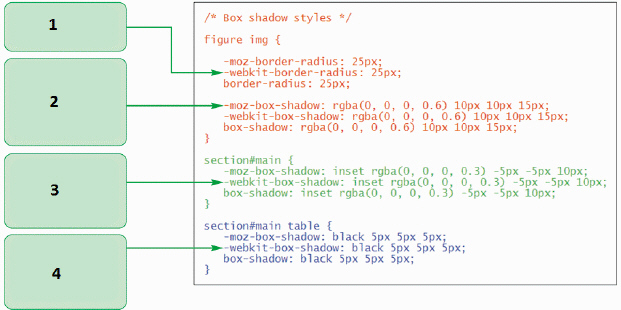 In the accompanying figure, which part adds an interior drop shadow to the lower-right corner of the main section with a blur radius of 10 pixels?
In the accompanying figure, which part adds an interior drop shadow to the lower-right corner of the main section with a blur radius of 10 pixels?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
When the Paste link option is used, a change in the destination file also appears in the source file
Indicate whether the statement is true or false
Computer Science & Information Technology