_________ controls access based on the identity of the requestor and on access rules stating what requestors are or are not allowed to do.
Fill in the blank(s) with the appropriate word(s).
DAC (discretionary access control)
You might also like to view...
PPP is a poor choice for an Internet-based remote access protocol because:
a. It does not utilize header compression b. PPP traffic is not encrypted c. PPP credentials are not encrypted d. It is not routable over IPv6 networks
Case-Based Critical Thinking QuestionsCase 6-1Kyra is designing a new Web page for her college volleyball team, and she receives some help from Max. He is not as experienced in Web design as Kyra is, and she provides a primer in terminology so they can clearly understand each other.Kyra wants to put the college's logo and team banner in the bar at the top of the page. What does she tell Max is the term for this space?
A. footer B. header C. sidebar D. navbar
Microsoft Xbox One is a type of ________
A) video game simulation B) video game system C) game controller D) game console
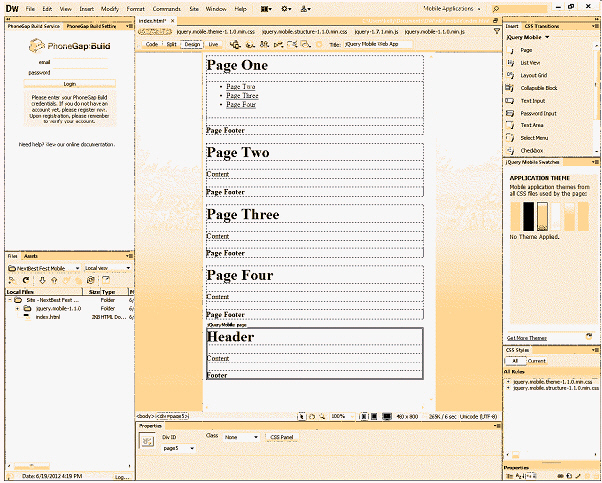 You can add new page divs to the site as shown in the accompanying figure using the ____ button in the jQuery Mobile category on the Insert panel.
You can add new page divs to the site as shown in the accompanying figure using the ____ button in the jQuery Mobile category on the Insert panel.
A. Div B. Tool C. Layer D. Page