32-bit operating system is capable of supporting up to _______ of RAM. ?Are these megabytes, gigabytes? -Michael
a. 2
b. 4
c. 8
d. 64
b.
You might also like to view...
How might the constraints in an information management plan be imposed on an organization?
Fill in the blank(s) with the appropriate word(s).
The first and getNext functions (the iterator) cannot be used in the deepCopy function because:
A. the first and getNext functions just return the elements within nodes, and the deepCopy function needs to know the address of the node to copy B. the deepCopy needs to know the address of each node in the original, so it can see which node the current pointer is set to; then, it can set the current pointer of the copy the same way C. a class function cannot call any other class functions D. the first and getNext functions are just used for searching
Which of the following is an example of a hash algorithm?
A) SHA B) AES C) RSA D) DES
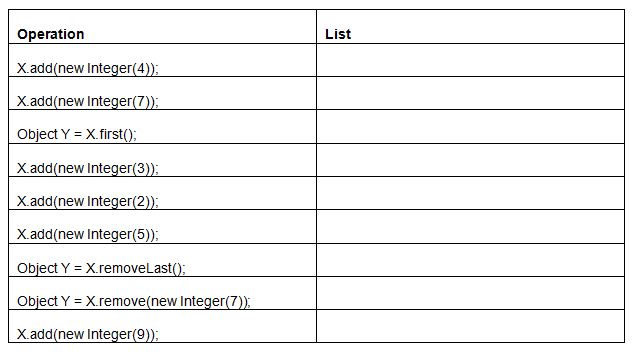
Hand trace an ordered list X through the following operations.
An ordered list keeps the items in order no matter when they are added. So the evolution of the list is as follows: