?
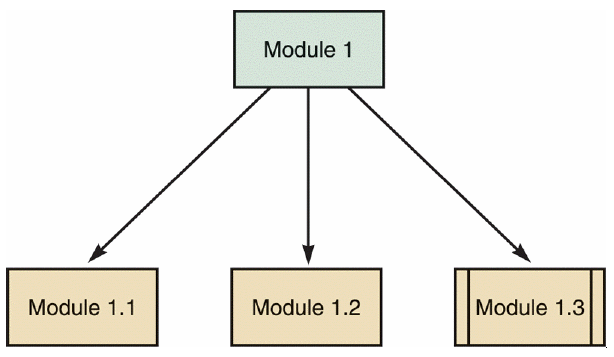
?The given figure shows a _____ module, which is reusable code and can be invoked from more than one point in a structure chart.
A. ?library
B. ?data
C. ?subordinate
D. ?control
Answer: A
You might also like to view...
Which of the Java strings represent the regular expression ,\s*?
a. "\,\s\*" b. ",\\s*" c. ",\\s\\*" d. ".\\s\*"
In the IA-32 architecture, a(n) ________ occurs when a process has attempted to access memory outside of its segment.
a) page fault b) general protection fault exception c) segment-overflow exception d) TLB miss
Match the following Conditional Formatting Options in the Quick Analysis Gallery with their description:
I. Text Contains II. Duplicate Values III. Unique Values IV. Equal To V. Clear Format A. Formats cells that have exactly the same value B. Formats any cell that has content that matches the first content in the first selected cell C. Removes any conditional formatting D. Formats cells that have no matching values E. Formats cells that have the value
Describe an example in which absolute denial of service to a user (that is, the user gets no response from the computer) is a serious problem to that user. Describe another example where 10 percent denial of service to a user (that is, the user’s computation progresses but at a rate 10 percent slower than normal) is a serious problem to that user. Could access by unauthorized people to a computing system result in a 10 percent denial of service to the legitimate users? How?
What will be an ideal response?