Before you modify an unselected path, you must select it with the ____________________ tool.
Fill in the blank(s) with the appropriate word(s).
Direct Selection
You might also like to view...
Modifying the Address Resolution Protocol (ARP) table for hacking purposes is called ____________________.?
Fill in the blank(s) with the appropriate word(s).
Create suitable names for Boolean variables to be used as flags. The variables will be true for each of the following situations and false otherwise. State names in a positive way and avoid including the terms not or no as part of the name.
When the variable value is equal to 100
Which of the following would be the device file for the third partition on the second SATA drive on a Linux system?
A. /dev/hdb3 B. /dev/hdc2 C. /dev/sdb3 D. /dev/sdc2
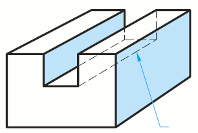 Images in the accompanying figure represent __________________ balance.
Images in the accompanying figure represent __________________ balance.
Fill in the blank(s) with the appropriate word(s).