The mens rea of criminal attempt is always
a. knowledge.
b. aid
c. abetting.
d. purpose.
d
You might also like to view...
Even if a privilege applies, you may still obtain the information if you have an appropriate release
Indicate whether the statement is true or false
Answer the following statement(s) true (T) or false (F)
1. Individuals involved in high-tech espionage are often industrial spies who sell their knowledge to rivals or foreign bidders. 2. Key loggers are secret programs that record a user’s keystrokes. 3. Both viruses and works can spread with no assistance. 4. Network scanning programs are used to find vulnerable networked computers. 5. “Phone-phreaking” refers to automatic speed dialers used by computer hackers.
From the following data, calculate the z-score.
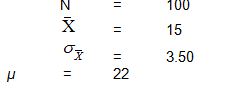
a.1.23
b.-1.23
c.2.00
d.-2.00
Weapons that are meant to incapacitate a suspect without inflicting serious injuries are called:
A) soft weapons. B) subdue and suppress weapons. C) non-fatal weapons. D) friendly-fire weapons. E) less-lethal weapons.