Products that earn the ENERGY STAR rating have
A) Highly efficient rates, low costs, and high availability
B) Low total energy requirements, low power modes, and efficient power supplies
C) Low battery and RAM requirements and no external power supply
D) High total energy requirements, high power modes, and highly efficient power supplies
B
You might also like to view...
Provide steps on how to review the logs.
After the attack, the users no longer have access to the file named confidential.txt. Now you will review the logs to determine how the file was compromised. Note: If this was a production network, it is recommended that analyst and root users change their passwords and comply with the current security policy.
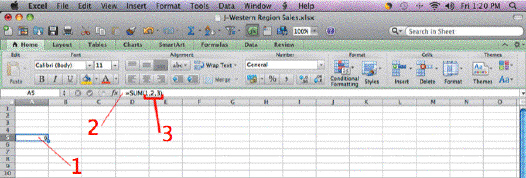 In the accompanying figure, Item 3 points to ____.
In the accompanying figure, Item 3 points to ____.
A. arguments B. criteria C. a mathematical operator D. a formula
The _____ is a top-down representation of a process.
A. Unified Modeling Language (UML) B. total cost of ownership (TCO) C. functional decomposition diagram (FDD) D. Rapid Economic Justification (REJ)
Which of the following is a best practice when securing a switch from physical access?
A. Disable unnecessary accounts B. Print baseline configuration C. Enable access lists D. Disable unused ports