An increasing concern for privacy and widespread availability of encryption products has led to the use of encryption for individual files and even entire devices. Briefly discuss the current state of encryption with respect to forensic investigation.
What will be an ideal response?
Although some encryption is poorly done and is easily broken, high-quality products are increasingly available that use good encryption algorithms beyond our current capability to reverse encryption by trying all possible combinations. Encrypted information poses significant challenges to forensic investigators because, by its nature, encryption conceals the content of digital material. Many encryption products require input of an encryption key when the user logs on and then decrypts the user's information on the fly. When the system goes into screen saver mode or is powered down, the encryption key is deactivated and must be reentered. Unfortunately, data needed by the forensic investigator will be encrypted and will not be readable without the proper key.
You might also like to view...
When an arrow side or other side significance is not intended, the seam-weld symbol is located ____ the reference line.
A. aside B. astride C. inside D. along
What instruments are needed to make a sketch or simple drawing?
What will be an ideal response?
In the accompanying figure, this jog circuit uses two momentary-contact pushbutton switches, and one _______________ switch.
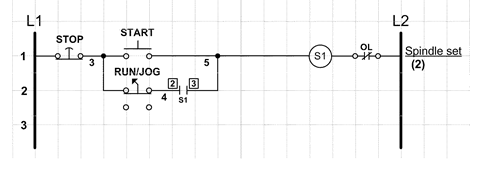
Fill in the blank(s) with the appropriate word(s).
An arc is always dimensioned by giving the ____.
A. radius B. tangent C. diameter D. perspective