What Windows permission should be used cautiously and only for exceptions?
A. Allow
B. Remove
C. Deny
D. Advanced
Answer: C
You might also like to view...
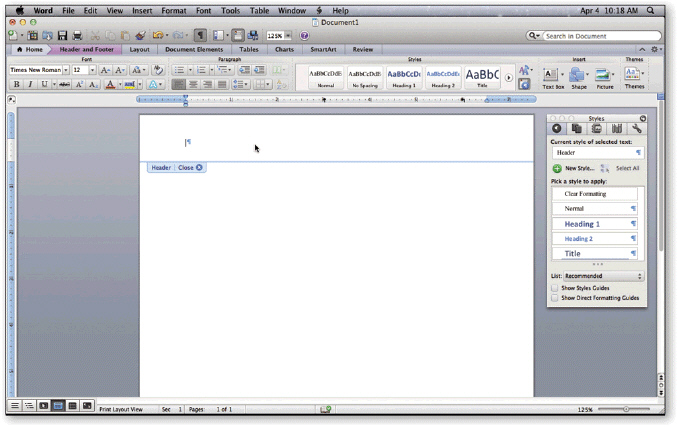 A(n) ____________________, like the one in the accompanying figure, is text and graphics printed at the top of each page in a document.
A(n) ____________________, like the one in the accompanying figure, is text and graphics printed at the top of each page in a document.
Fill in the blank(s) with the appropriate word(s).
Match the grammar or spelling error with the Office 2013 identification or button to click:
I. you write "there" instead of "their" II. you write "recieve" instead of "receive" III. you leave out a necessary comma IV. you want it to not stop on your name in the future V. you want to bypass all occurrences of "daycare" A. Ignore All B. red wavy underline C. green underline D. blue underline E. Add to Dictionary
It is a good idea to verify external hyperlinks on an ongoing basis.
Answer the following statement true (T) or false (F)
Briefly describe traffic filtering.
What will be an ideal response?