Diffie-Hellman provides secure key distribution, confidentiality, authentication, and nonrepudiation
Indicate whether the statement is true or false.
False Diffie-Hellman provides secure key distribution, but not confidentiality, authentication, or nonrepudiation.
You might also like to view...
Define what a network is, discuss its advantages, and briefly explain the main types of networks.
What will be an ideal response?
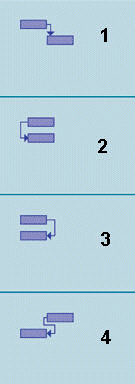 In the event of a power interruption, the UPS must start before the operator can finish shutting down the system in an orderly fashion; this relationship between these two tasks is an example of the task dependency type marked ____ in the accompanying figure.
In the event of a power interruption, the UPS must start before the operator can finish shutting down the system in an orderly fashion; this relationship between these two tasks is an example of the task dependency type marked ____ in the accompanying figure.
A. 1 B. 2 C. 3 D. 4
Complete the program below that calculates the surface area and volume of a rectangular solid based on its length, width, and height. Define function rectangleAreaVolume.
#includeusing namespace std; // Put your function prototype here. int main() { double length; double width; double height; double sArea; double vol; cout << "Enter the length of the rectangular solid => "; cin >> length; cout << "Enter the width of the rectangular solid => "; cin >> width; cout << "Enter the height of the rectangular solid => "; cin >> height; rectangleAreaVolume( __________________, ___________________, ____________________, ____________________, _________________ ); cout << "Surface area = " << sArea << " square units." << endl; cout << "Volume = " << vol << " cubic units." << endl; return 0; } // Calculates the surface area and volume of a rectangular solid. // Put your function definition here.
What advanced command-line interface serves as a front end for specialized commands, known as cmdlets?
A. Command Prompt B. Windows Bash C. PowerShell D. Z Shell