Typically, infected attachments look like _____ files, and they infect your computer when you open them.
A. video
B. audio
C. document
D. executable
Answer: D
Computer Science & Information Technology
You might also like to view...
When you cut or copy text, you are also copying the ________ of that text
Fill in the blank(s) with correct word
Computer Science & Information Technology
Which process injects invalid or unexpected input (sometimes called faults) into an application to test how the application reacts?
A. buzzing B. fuzzing C. stress testing D. input validation
Computer Science & Information Technology
?
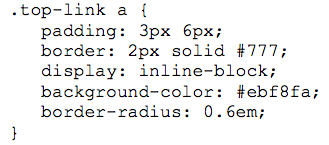
A. padding: B. border: C. display: D. border-radius:
Computer Science & Information Technology
In general, you should use thenumber()function for numbering the nodes in the result document.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology