A discarded credit card receipt may become the starting point from which an identity fraud perpetrator finds enough information to assume the victim's identity
Indicate whether the statement is true or false.
True
Computer Science & Information Technology
You might also like to view...
What role does the virtual file system (VFS) perform within the CentOS 7 kernel?
What will be an ideal response?
Computer Science & Information Technology
In Word, the Spacing After setting adds space after sentences and between paragraphs
Indicate whether the statement is true or false
Computer Science & Information Technology
In the accompanying figure of a Microsoft Access 2016 document, which of the following boxes is pointing to the Property Sheet button??
?
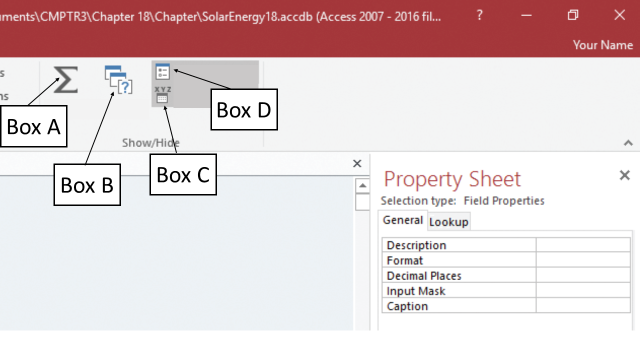
A. Box A? B. ?Box B C. ?Box C D. ?Box D
Computer Science & Information Technology
In 1998, ethnic Tami guerrillas swamped _________ embassies with 800 emails a day
a. Chinese b. Iraqi c. Sri Lankan d. None of the above
Computer Science & Information Technology