A(n) ____________________ is a weakness in an information system, system security procedures, internal controls, or implementation that could be exploited by a threat source.
Fill in the blank(s) with the appropriate word(s).
vulnerability
Computer Science & Information Technology
You might also like to view...
Which of the following correctly declare 3 integer pointers?
a. int* p1, p2, p3; b. int *p1, p2, p3; c. int *p1, *p2, *p3; d. all of the above.
Computer Science & Information Technology
Which of the following choices includes the development of the policies that shape the project management process?
A. Review process B. Quality process C. Development process D. Strategic planning process
Computer Science & Information Technology
Write a new method to maximize blue (i.e., setting it to 255) instead of clearing it use Program 7 as a starting point.
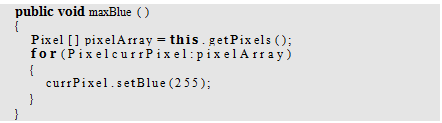
Is this useful? Would the red or green versions be useful?
Computer Science & Information Technology
How is text aligned by default?
A) Decimal B) Left C) Right D) Center
Computer Science & Information Technology