Why do many people dismiss the topic of embedded device security?
What will be an ideal response?
Many dismiss the topic of embedded device security to focus on more popular security issues. Most of the media emphasis is on threats that people can understand and relate to, such as the latest network worm, or the most recent Facebook application attack. However, embedded systems are in all networks and perform essential functions, such as routing network traffic and blocking suspicious packets.
You might also like to view...
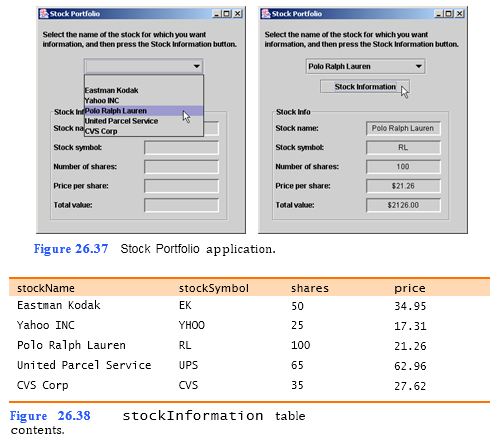
A stockbroker wants an application that will display a client’s stock portfolio (Fig. 26.37). All the companies that the user holds stock in should be displayed in a JComboBox when the application is loaded. When the user selects a company from the JComboBox and clicks the Stock Information JButton, the stock information for that company should be displayed in output JTextFields. The provided stocks database contains one table, stockInformation (Fig. 26.38), which has four columns—stockName, stockSymbol, shares and price. The values stored in the stockName and stockSymbol col- umns are Strings. The values stored in the shares column are ints. The values stored in the price column are doubles.
a) Copying the template to your working directory. Copy the C:Examples Tutorial26ExercisesStockPortfolio directory to your C:SimplyJava directory.
b) Copying the database to your working directory. Copy the stocks database directory from C:ExamplesTutorial26ExercisesDatabases to your C:Simply- JavaStockPortfolio directory.
c) Opening the template file. Open the StockPortfolio.java file in your text editor. d) Declaring instance variables for database processing. In line 45, declare three
instance variables—myConnection, myStatement and myResultSet—of types Con-
nection, Statement and ResultSet, respectively.
e) Adding a database connection and creating a Statement object. In line 52 in the StockPortfolio constructor, insert statements that load the database driver, connect to the stocks database and create a Statement for submitting SQL to the database. Assume that the driver class name and JDBC URL are passed to the constructor
The ____________________ diagram graphically highlights the interdependencies of tasks.
Fill in the blank(s) with the appropriate word(s).
It's important for designers to test their solutions for effective results
Indicate whether the statement is true or false
When the destructor ____ the queue, it deallocates the memory occupied by the elements of the queue.
A. allocates B. instantiates C. destroys D. rebuilds