Which of the following protocols provides encryption to protect the data as it is transmitted over the network?
A. HTTP
B. SHTTP
C. FTP
D. TFTP
E. SFTP
F. options a and b only
G. options c, d, and e only
H. options a and c only
I. options b and e only
J. all of the options
I
Explanation: Only SHTTP and SFTP provide encryption to protect the data as it is transmitted over the network.
None of the other options provides encryption.
You might also like to view...
Match each item with a statement below.
A. A connectionless protocol that uses IP to get packets from one computer to another. B. A connectionless protocol used for sending and receiving requests between the client and server on a network. C. A protocol used to generate IP error messages. D. A protocol used to send e-mail in user-level client applications. E. A virtual terminal protocol for connecting to a remote computer. F. A protocol used to map a fully qualified domain name with an IP address. G. A connection-oriented protocol responsible for keeping track of packets and reassembling them into a single file after they have all arrived. H. A protocol used to move files from one computer to another efficiently and accurately. I. A protocol that handles the delivery of data as packets.
Which of the following is the file extension for a theme template
A) .thex B) .thms C) .tmex D) .thmx
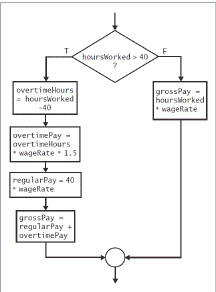 The flowchart in the accompanying figure depicts a ____.
The flowchart in the accompanying figure depicts a ____.
A. dual-outcome selection with multiple actions B. dual-outcome selection C. selection structure contained in a sequence structure. D. single-outcome selection
The Sort dialog box allows you to sort text is all of the following ways EXCEPT:
A) by date B) by number C) alphabetically D) by time