A(n) ____ involves determining the damage that would result from an attack and the likelihood that a vulnerability is a risk to the organization.
A. threat modeling
B. risk assessment
C. attack tree
D. attack modeling
Answer: B
You might also like to view...
When deriving from a class with protected inheritance, public members of the base class become members of the derived class, and protected members of the base class become members of the derived class.
Fill in the blank(s) with the appropriate word(s).
The order that the logical tests are entered into a nested IIF Function are irrelevant because Access will make the necessary adjustments
Indicate whether the statement is true or false
Another name for the notification area on the right side of the taskbar that displays the status of your computer, shortcuts, and a clock is the:
A) system tray B) Quick Launch toolbar C) taskbar D) Windows Sidebar
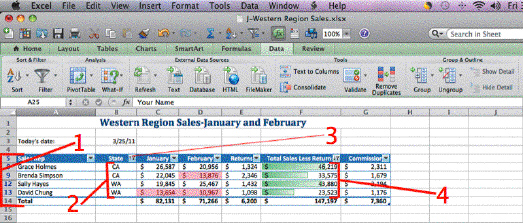 In the accompanying figure, Item 2 points to a column that shows that only the ____ for CA and WA have been marked in a filtered list of states.
In the accompanying figure, Item 2 points to a column that shows that only the ____ for CA and WA have been marked in a filtered list of states.
A. pop-up arrows B. check boxes C. data tabs D. dialog boxes