A wireless security toolkit should include the ability to sniff wireless traffic, scan wireless hosts, and assess the level of privacy or confidentiality afforded on the wireless network. _________________________
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
The ________________________________________ topology consists of ad hoc peer-to-peer communication between WNICs on individual computers.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
To select the ROUND function, you click the ________ button in the Function Library group on the Formulas tab
A) Trig B) Statistics C) Math & Trig D) Math & Statistics
Computer Science & Information Technology
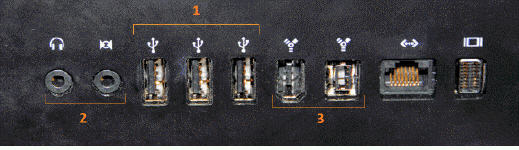 In the accompanying figure of computer ports, Item 2 indicates the ____ ports.
In the accompanying figure of computer ports, Item 2 indicates the ____ ports.
A. USB B. audio C. FireWire D. mini-DVI
Computer Science & Information Technology
_____ prevents unauthorized users from creating, modifying, or deleting information.
A. Availability B. Integrity C. Confidentiality D. Evacuation
Computer Science & Information Technology