A(n) ________ virus runs a program that searches for common types of data files, compresses them, and makes them unusable.
What will be an ideal response?
encryption; ransomware
You might also like to view...
The default text box font is ____.
A. Arial B. Times New Roman C. Calibri D. Cambria
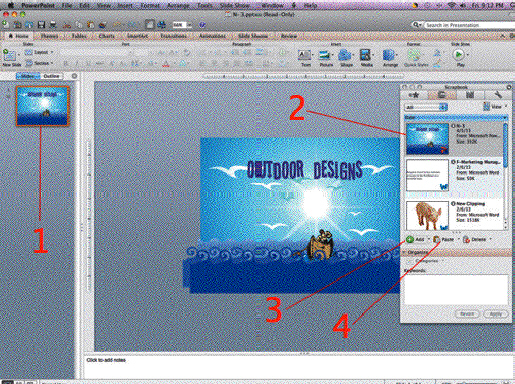 In the accompanying figure, Item 1 points to a(n) ____.
In the accompanying figure, Item 1 points to a(n) ____.
A. selected slide added to the Scrapbook as a clip B. Rich Text Format slide C. selected slide D. expanded slide
What are the questions you need to ask when planning the justification step of a business case?
What will be an ideal response?
Joe, the chief technical officer (CTO) is concerned that the servers and network devices may not be able to handle the growing needs of the company. He has asked his network engineer to being monitoring the performance of these devices and present statistics to management for capacity planning. Which of the following protocols should be used to this?
A. SNMP B. SSH C. TLS D. ICMP