Ethical hacking does not always require the explicit permission of the owner of the target.
a. true
b. false
b. false
You might also like to view...
When changing the slide background, the Transparency value controls the brightness and contrast of the selected Stop color
Indicate whether the statement is true or false
Folders can only be created in File Explorer, not within software programs
Indicate whether the statement is true or false
You want to sort table data in such a way that the zip code column is arranged in ascending order, with the last name column sorted alphabetically within zip code. Which of those columns would be considered the primary category in a sort procedure?
What will be an ideal response?
?
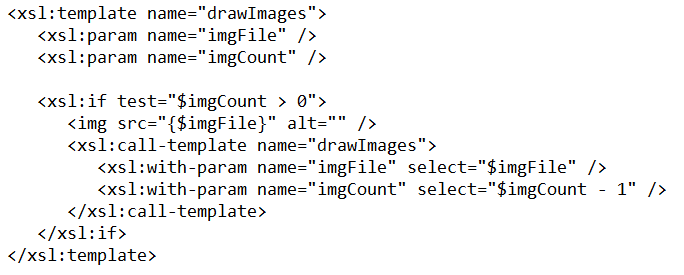
A. ?