How are alterations to mission critical servers approved before implementation when a change management process is involved?
A. By providing a rollback option
B. By showing a less than 10% chance of failure
C. By being assessed by a Change Control Board
D. By documenting all changes that will take place
Answer: C. By being assessed by a Change Control Board
You might also like to view...
Answer the following statements true (T) or false (F)
1. Disk drives and record able optical disk drives can be considered input devices or output devices. 2. There are two general categories of software: system software and utility software. 3. Software development tools control the internal operations of the computer’s hardware, mange all the devices connected to the computer, allow data to be saved to and retrieved from the storage devices, and allow other programs to run on the computer. 4. Examples of utility programs are virus scanners, file-compression programs, and data-backup programs.
The relation shown in Figure 15.12 describes hospitals (hospitalName) that require certain items (itemDescription), which are supplied by suppliers (supplierNo) to the hospitals (hospitalName). Furthermore, whenever a hospital (h) requires a certain item (i) and a supplier (s) supplies that item (i) and the supplier (s) already supplies at least one item to that hospital (h), then the supplier (s) will also be supplying the required item (i) to the hospital (h). In this example, assume that a description of an item (itemDescription) uniquely identifies each type of item.
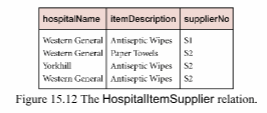
(a) Describe why the relation shown in Figure 15.12 is not in 5NF.
(b) Describe and illustrate the process of normalizing the relation shown in Figure 15.12 to 5NF.
When using the rand() function, how do you ensure that you will obtain the same series of numbers?
A. Pass srand() the same seed value. B. Call it from a different location in the code. C. Use the modulus operator with a different number after it. D. You can’t. You always obtain random numbers.
If you replace text in a page that is not currently open, you can undo it.
Answer the following statement true (T) or false (F)