One way to program ladder instructions is to drag and drop them from the ____________________ toolbar to the desired position on a ladder rung or select where to place the instruction on the rung and simply click it on the toolbar.
Fill in the blank(s) with the appropriate word(s).
Language Element
You might also like to view...
The first time you configure a DNS server, the forwarder list ____.
A. points to the slave name server B. contains the loopback address C. does no exist D. is empty
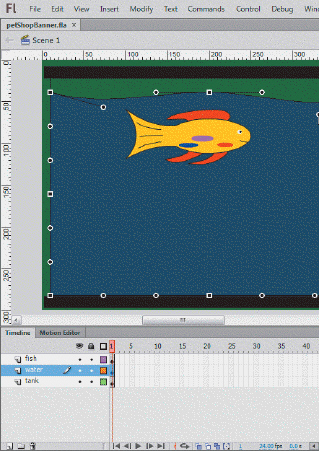 Referring to the accompanying figure, the transformation handles are circles.
Referring to the accompanying figure, the transformation handles are circles.
Answer the following statement true (T) or false (F)
What is a zero-day attack?
A. Attacks that come after fixes are released are called zero-day attacks. B. Security weaknesses that open a program to attack. C. Attacks that come before fixes are released are called zero-day attacks. D. Aprogram that takes advantage of a vulnerability to allow the attacker to take over the computer or at least an individual account.
&grade[3] is equivalent to ____; assume that grade is an array of integers, and each integer requires 4 bytes of storage..
A. &grade[0] + 3 B. &grade[0] + 4 C. &grade[0] + (3 * 4) D. &grade[0] + (3 / 4)