In a procedure known as ____________________, an organization verifies that new mobile devices appearing in the organization's infrastructure are secure and safe to use within the organization.
Fill in the blank(s) with the appropriate word(s).
on boarding
You might also like to view...
Which of the following types of video files is used by QuickTime?
A. WMV B. FLV C. MOV D. AVI
Discuss two possible implementations of EN(e) and SN(s). Why must the intersection of EN(e) and SN(s) be non-null for a given e that matches s (the intersection rule)? Does this apply in your possible implementations?
What will be an ideal response?
By default, formulas use a relative cell reference
Indicate whether the statement is true or false
Case Question 2Natalie is responsible for updating her company's Web site. Her boss has asked her to choose and apply three different table styles as possible changes to existing tables. She is instructed to take screenshots of each style and bring the images to the next company meeting along with her comments and an overall recommendation.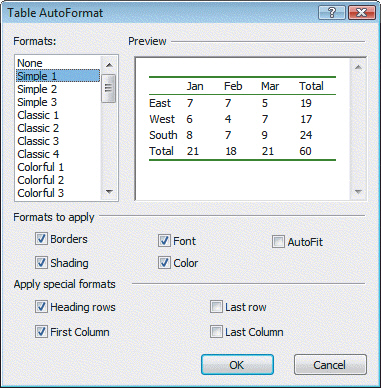 Referring to the figure above, what does the dialog box indicate about Natalie's selection?
Referring to the figure above, what does the dialog box indicate about Natalie's selection?
A. She chose to AutoFit the table's contents. B. She chose to apply special formats to all cells. C. She chose the Simple 1 rule. D. She chose a predesigned table format.