________ validation can be used to apply multiple validation criteria to a cell
A) Compound B) Complex C) Detailed D) Custom
D
You might also like to view...
What will be displayed when the following lines are executed? Dim x As Double = 3, y As Double = 1 Dim z As Double z = x + (y * x) x = y z = x + z lstBox.Items.Add(x + y + z)
(A) 4 (B) 9 (C) 10 (D) None of the above
Answer the following statements true (T) or false (F)
1. The legal and ethical aspects of computer security encompass a broad range of topics. 2. Computer attacks are considered crimes but do not carry criminal sanctions. 3. “Computers as targets” is a form of crime that involves an attack on data integrity, system integrity, data confidentiality, privacy, or availability. 4. The relative lack of success in bringing cybercriminals to justice has led to an increase in their numbers, boldness, and the global scale of their operations. 5. No cybercriminal databases exist that can point investigators to likely suspects.
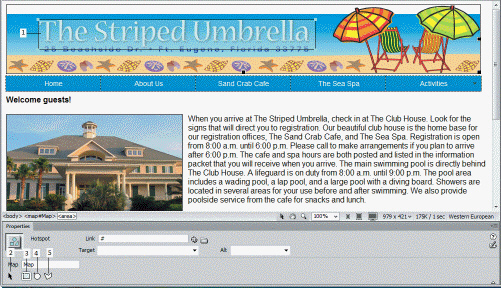 In the accompanying figure, Item 5 refers to the ____.
In the accompanying figure, Item 5 refers to the ____.
A. Active Hotspot Tool B. Circle Hotspot Tool C. Polygon Hotspot Tool D. Pointer Hotspot Tool
Which queue operation does the following algorithm describe?Algorithm aQueueOperation allocate queue head set queue front to null set queue rear to null set queue count to 0 return queue headend aQueueOperation
A. empty queue B. dequeue C. create queue D. queue count