Match each item with the correct statement below.
A. The font used by most law firms is
B. Contains contact information, purpose, and share structure of a company.
C. A template that contains line numbers and a double ruling at the left margin and a single ruling at the right margin.
D. Letter is written to this state official requesting to reserve the use of specific business names.
E. Legal documents vary by
F. The variable information in merging is stored in what type of file?
G. A letter of attorney authorizing representation to act on another's behalf in a legal matter.
H. A person who is licensed by the state to perform acts in legal affairs such as witnessing signatures on documents.
I. Marks a location in a document so that you can quickly move the insertion point to the location.
J. The testimony of a witness taken under oath.
A. Times New Roman
B. Articles of Incorporation
C. Pleadings
D. Secretary of State
E. State
F. Data
G. Power of Attorney
H. Notary
I. Bookmark
J. Deposition
You might also like to view...
Cascading Style Sheets (CSS), the style sheet language developed for use with HTML on the Web, also can be used with the elements in any XML document.
Answer the following statement true (T) or false (F)
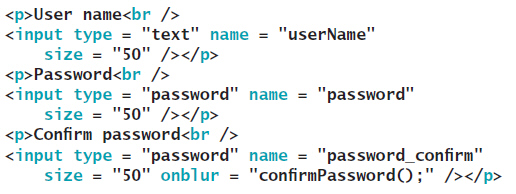 Which of the following might be found in the confirmPassword() function referenced in the accompanying figure in order to verify that the password and confirm password are the same?
Which of the following might be found in the confirmPassword() function referenced in the accompanying figure in order to verify that the password and confirm password are the same?
A. if (document.password_confirm.value == document.password.value) B. if (document.forms[1].password.value != document.forms[0].password.value) C. if (document.forms[0].password_confirm.value != document.forms[0].password_confirm.value) D. if (document.forms[0].password_confirm.value != document.forms[0].password.value)
Packet sniffing and ________ have proved to be favorite targets of organizations like EPIC and the ACLU
a. data mining b. anonymizer-type technology c. over-the-counter encryption technology d. disposable e-mail accounts
Case Based Critical ThinkingCase 1You are in charge of making your design firm's next project accessible to as many users as possible. Answer the following questions. Which section of the Rehabilitation Act of 1973 will you want to read?
A. 508 B. 58 C. 580 D. 5800