With ______ encryption each vulnerable communications link is equipped on both ends with an encryption device.
Fill in the blank(s) with the appropriate word(s).
link
You might also like to view...
Explain why a class might provide a set function and a get function for a data member.
What will be an ideal response?
When a template is opened from the New tab in the Backstage view, it is opened as a(n):
A) workbook. B) template. C) worksheet. D) object.
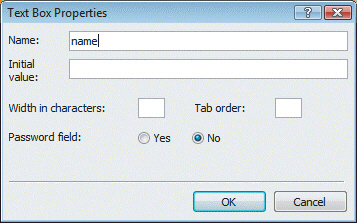 Referring to the figure above, you can use this dialog box to designate a password field, which ____.
Referring to the figure above, you can use this dialog box to designate a password field, which ____.
A. means that as a visitor enters information it will be displayed on the screen as asterisks B. is used by form-handling scripts C. provides default text that is displayed when the form is loaded D. dictates the width of the displayed text box
You can use the ____ Tool to drag to select a row of pixels across an image.
a. Single Row Marquee b. Cross-Image c. Pixel Row d. Magnetic Lasso