________ allows you to share copies of a presentation, ask for feedback, and then merge the copies with the original
Fill in the blank(s) with correct word
Track changes
You might also like to view...
A computer ____________________ is any person who designs, configures, analyzes, develops, tests, or ensures the security of computer hardware or software.
Fill in the blank(s) with the appropriate word(s).
Match the following terms with their definitions
I. Navigational flicks II. Bezel gestures III. Touch gestures IV. Editing flicks V. Gesture A. A gesture that start and/or ends at the edge of the screen. B. Quick short gestures that either scroll or move forward or backward a page. C. Quick short gestures in a diagonal direction that either delete, copy, paste or undo. D. Gestures made with a finger. E. A movement of the user's finger, fingers or pen on a touch screen.
FIGURE EX 5-1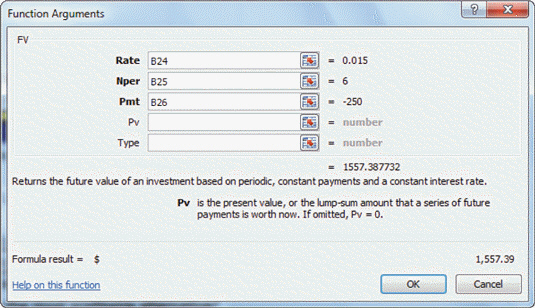 In Figure EX 5-1 above, the Pmt figure is -250. The negative number means ____.
In Figure EX 5-1 above, the Pmt figure is -250. The negative number means ____.
A. the entry is income B. the entry is a payment C. there is an error D. the person is behind on their payments
The __________ vulnerability assessment is designed to find and document vulnerabilities that may be present in the organization's public network.
Fill in the blank(s) with the appropriate word(s).