The Information or Digital Revolution has exacerbated the vulnerabilities of government institutions and personal residences alike
Indicate whether the statement is true or false.
Answer: True
You might also like to view...
Answer the following statements true (T) or false (F)
1. End-user device analytics is a method of QoE measurement. 2. The full-reference black-box quality models are widely used for onsite bench marking, diagnosis, and tuning of network equipment, where clean stimulus is available. 3. The glass-box parameter-based models are generally less accurate and coarser than black-box media-based ones. 4. The network layer QoS/QoE mapping models rely solely on NQoS metrics gathered from the TCP/IP stack. 5. The service-oriented actionable QoE solutions account for QoE measures within the delivery infrastructure.
The relation shown in Figure 15.11 lists members of staff (staffName) working in a given ward (wardName) and patients (patientName) allocated to a given ward. There is no relationship between members of staff and patients in each ward. In this example assume that staff name (staffName) uniquely identifies each member of staff and that the patient name (patientName) uniquely identifies each patient.
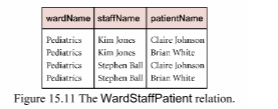
(a) Describe why the relation shown in Figure 15.11 is in BCNF and not in 4NF.
(b) The relation shown in Figure 15.11 is susceptible to update anomalies. Provide
examples of insertion, deletion, and update anomalies.
(c) Describe and illustrate the process of normalizing the relation shown in Figure 15.11 to 4NF.
The _____________ operator returns false if the left operand is greater than the right oper- and.
a) == b) < c) <= d) All of the above
Minimum password length, password age, and password history are defined in which of the following?
a. Administrative policies b. User policies c. Computer policies d. Technical policies