What security principle limits access to services to only those needed, keeping all other ports closed?
What will be an ideal response?
Least privilege
Computer Science & Information Technology
You might also like to view...
A heap is a complete binary tree. What is required for the tree to be complete?
What will be an ideal response?
Computer Science & Information Technology
After the customized image is created, it is placed on a distribution share by using Windows __________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Configure the IP address settings for the router (R1), the computers (PC1 and PC2), and the switch (S1) for the network provided in Figure 1. Use the IP addresses provided in Table 1.
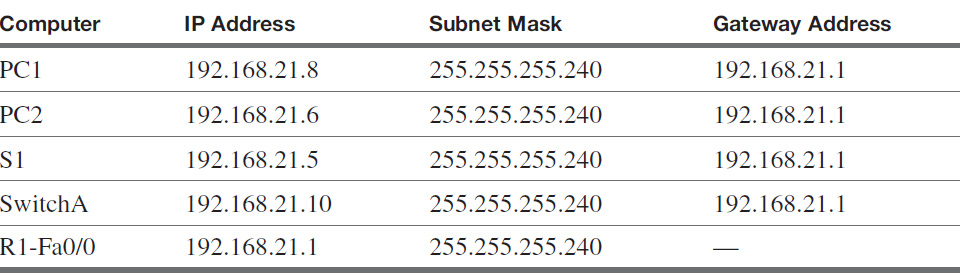
Computer Science & Information Technology
A workbook marked as final is read-only
Indicate whether the statement is true or false
Computer Science & Information Technology