A network administrator receives a call asking for assistance with connecting to the network. The user asks for the IP address, subnet class, and VLAN required to access the network. This describes which of the following attacks?
A. Social engineering
B. Spoofing
C. Zero-day attack
D. VLAN hopping
Answer: A. Social engineering
You might also like to view...
The one single aspect of the conventional data processing operation that is certain to require definition from a forensic perspective is the ____ policy.
A. data retention B. data loss C. data security D. data integrity
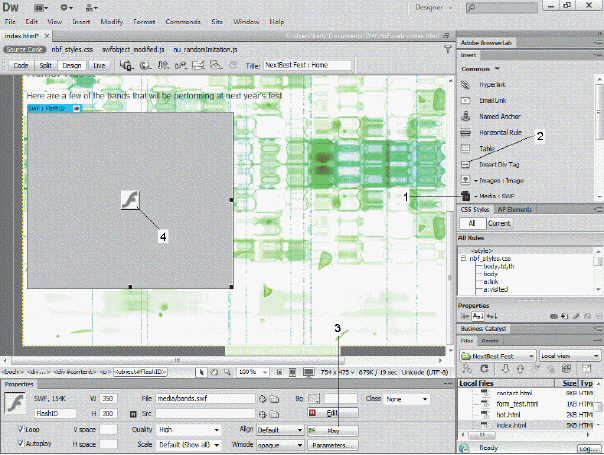 When you save the home page in the accompanying figure, the Copy Dependent Files dialog box opens, stating that the page uses a(n) ____ that requires supporting files that have been copied to the local site.
When you save the home page in the accompanying figure, the Copy Dependent Files dialog box opens, stating that the page uses a(n) ____ that requires supporting files that have been copied to the local site.
A. object B. behavior C. event D. either a or b
You can define a numeric array named custNumber with 10 elements like this:Declare Numeric custNumber = 10
Answer the following statement true (T) or false (F)
A mechanical or electronic device designed to secure, hold, or close items operated by a key, combination, or keycard is a ________.
What will be an ideal response?