The more layers in a file, the larger the file size, and therefore ____ layers is used to reduce file size.
A. consolidating
B. merging
C. flattening
D. drafting
Answer: B
You might also like to view...
Behavior that falls within the common norms of a group is known as ____ behavior.
A. acceptable B. unacceptable C. tolerable D. functional
An attacker gains unauthorized access to a virtual server in a public cloud. Which of the following statements about the attack can be true?
a. The attacker is an anonymous, non-trusted cloud service consumer. b. The attacker is a cloud service consumer that resides outside of the cloud, in an on-premise environment. c. The attacker is a cloud service consumer that resides in a different cloud. d. All of the above.
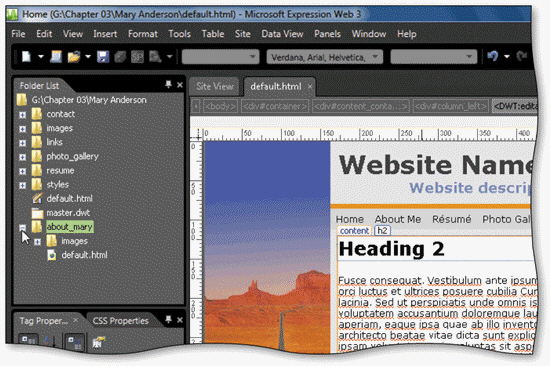 The ____ sign or symbol to the left of a folder name in the Folder List indicates that the folder is expanded to show its contents, as shown in the accompanying figure.
The ____ sign or symbol to the left of a folder name in the Folder List indicates that the folder is expanded to show its contents, as shown in the accompanying figure.
A. plus (+) B. minus (-) C. asterisk (*) D. at (@)
The amount of work of a logarithmic algorithm is proportional to the log2 of the problem size.
Answer the following statement true (T) or false (F)