Identify, prioritize, and plan for the top five risks related to the user interface subsystem of CTC presented in Chapter 12, Rationale Management.
What will be an ideal response?
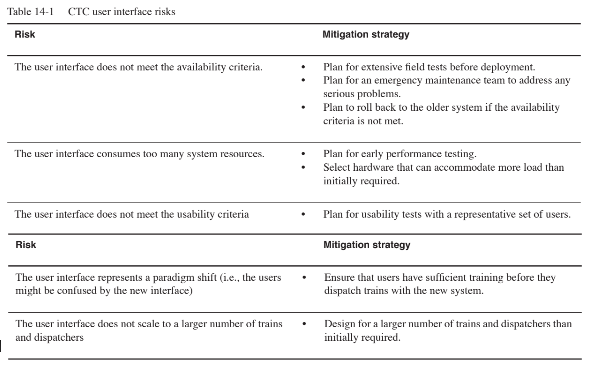
Same exercise as before with a different application domain. Table 14-1 depicts an example solution.
You might also like to view...
A pixel with full saturation is a neutral gray.
Answer the following statement true (T) or false (F)
In SharePoint, the ________ list enables you to group messages and responses in the order in which they arrived, or by threads
Fill in the blank(s) with correct word
Once a paragraph is selected, choosing the fill color red in the Shading tab of the Borders and Shading dialog box ________
A) makes the paragraph text red B) highlights the paragraph text in red C) makes the paragraph border red D) makes the page border red
Which of the following is most associated with the concept of converged networks?
a. More users wanting to access web pages in character mode b. More voice and video transmissions that require a level of consistent quality and uninterrupteddelivery c. More networks that are locked down so that new applications and services cannot be added d. More networks that are open and unconcerned with protection from unauthorized access