Discuss at least two security advantages of a host running virtualization.
What will be an ideal response?
The latest security updates can be downloaded and run in a virtual machine to determine compatibility. A snapshot of a state of a virtual machine can be saved for later use. Testing the existing security configuration, known as security control testing, can be performed using a simulated network environment on a computer using multiple virtual machines. Virtual machines can promote security segregation and isolation. A virtual machine can be used to test for potential malware.
You might also like to view...
Which of the following statements is true?
``` public class TestA { public static void main(String[] args) { int x = 2; int y = 20 int counter = 0; for (int j = y % x; j < 100; j += (y / x)) { counter++; } } } public class TestB { public static void main(String[] args) { int counter = 0; for (int j = 10; j > 0; --j) { ++counter; } } } ``` a. The value of counter will be different at the end of each for loop for each class. b. The value of j will be the same for each loop for all iterations c. Both (a) and (b) are true. d. Neither (a) nor (b) is true.
What is the error in the following code? Why is this wrong?
``` int f(int x) { int x; // code for function body } ``` What will be an ideal response?
Is this server a stateful server? If so, what kind of state information (global or session) does it maintain?
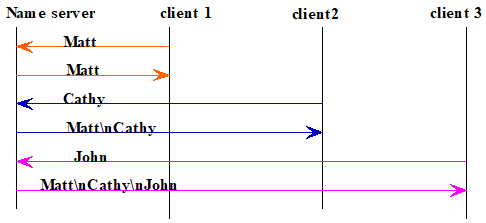
Using the three-tier software architecture presented in this chapter, design and implement a client-server suite for the following protocol (it is not a well-known service): Each client sends to the server a name. The server accumulates the names received from successive clients (by appending each, with a linefeed (‘
’), to a static string). Upon receiving a name, the server sends the names that it has collected to the client. The figure below illustrates the sequence diagram of a session of the protocol.
A proportional typeface has characters that ________
A) vary in width B) are the same width C) have an absolute position D) have a relative position