Dual in-line memory modules (DIMMs) are available in all the following pin sizes except for ________?
a. 168 pin
b. 184 pin
c. 240 pin
d. 268 pin
D. Dual in-line memory modules are available in 168-pin, 184-pin, 240-pin, and 288-pin versions.
You might also like to view...
What menu is used to align controls on a form?
(A) View (B) Window (C) Build (D) Format
Create an application that allows a user to reserve a car for the specified day (Fig. 25.52). The car reservation company can rent out only four cars per day. Let the application allow the user to specify a certain day. If four cars have already been reserved for that day, then indicate to the user that no vehicles are available. Reserva- tions are stored in reservations.txt.
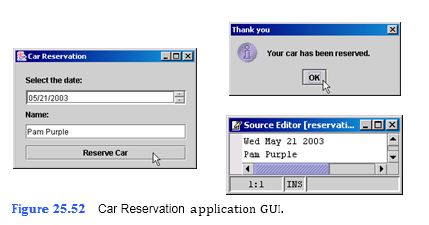
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial25ExercisesCarReservation to your C:SimplyJava directory.
b) Opening the template file. Open the CarReservation.java file in your text editor. c) Declaring a BufferedReader and a PrintWriter instance variable. At line 24,
declare two instance variables—a BufferedReader object named input, which will
be used to read from a file, and a PrintWriter object named output, which will be used to write to a file.
d) Opening a file to read from. In the reserveCarJButtonActionPerformed method (which immediately follows createUserInterface), create a new File object reserveFile for the file reservations.txt. Then, add a try block. Inside the try block, create a FileReader by passing the reserveFile to its constructor . Use this FileReader to initialize BufferedReader input.
e) Retrieving the selected date. For this application, you should store in reserva- tions.txt the date selected
Pressing Ctrl while dragging an object makes the object move in a straight line
Indicate whether the statement is true or false
Which of the following authentication methods measure unique human characteristics to confirm identity?
A. Smart cards B. Tokens C. Biometrics D. PINs