Where are Trust Center options located?
A) Insert tab B) Data tab C) Backstage D) Formulas tab
C
Computer Science & Information Technology
You might also like to view...
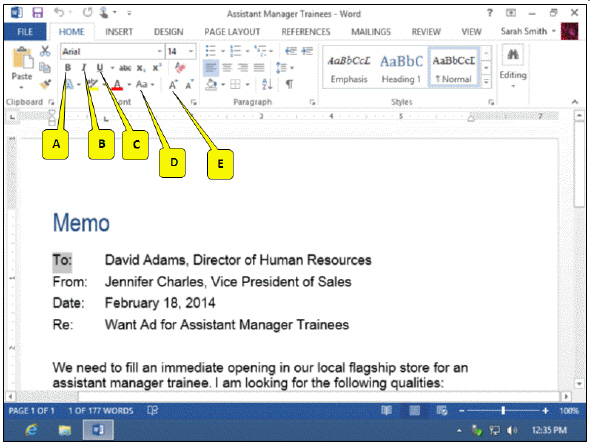 Refering to the accompanying figure, which callout points to the Italic button?
Refering to the accompanying figure, which callout points to the Italic button?
A. E B. B C. D D. A
Computer Science & Information Technology
Decision makers are beginning to understand that ________ is not just a byproduct of conducting business, but a critical factor in determining the success or failure of a business.
A) information B) decoration C) hesitation D) frustration
Computer Science & Information Technology
If an attacker breaks into a corporate database and steals critical files then deletes the files, against what security goal/s is this attack aimed
A. Confidentiality and Availability B. Confidentiality only C. Integrity and Confidentiality D. Availability and Integrity
Computer Science & Information Technology
Change the percent to a fraction. Reduce it to its lowest terms. ![]()
A. ![]()
B. ![]()
C. ![]()
D. ![]()
E. ![]()
Computer Science & Information Technology