___________ tasks allow custom code to be executed to extend the functionality of the basicset of tasks.
Fill in the blank(s) with the appropriate word(s).
Scripting
You might also like to view...
Defense in depth can best be described as which of the following?
A. a firewall that protects the network and the servers B. a layered approach to security C. antivirus software and firewalls D. authentication and encryption
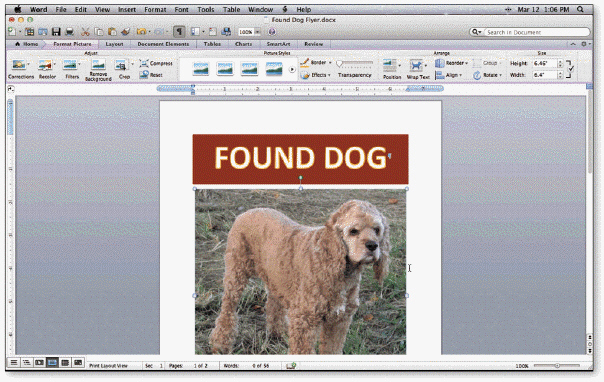 _________________________ includes both enlarging and reducing the size of a graphic, as shown in the accompanying figure.
_________________________ includes both enlarging and reducing the size of a graphic, as shown in the accompanying figure.
Fill in the blank(s) with the appropriate word(s).
Expression Values refers to spelling, grammar, and sequence of characters in a programming language
Indicate whether the statement is true or false
One of the most fundamentally important virtues of a(n) ____________________ is that if we can specify one to solve a problem, then we can automate the solution.
Fill in the blank(s) with the appropriate word(s).