_________ is accessing someone else's unsecured Wi-Fi network from the hacker's current location without authorization.
A. Wi-Fi piggybacking
B. Wi-Fi wardriving
C. Wi-Fi cyberterrorism
D. Wi-Fi maneuvering
Fill in the blank(s) with the appropriate word(s).
Wi-Fi piggybacking
Rationale: Unauthorized use of a Wi-Fi network is called war driving or Wi-Fi piggybacking, depending on the location of the hacker at the time. Wi-Fi piggybacking is accessing someone else's unsecured Wi-Fi network from the hacker's current location without authorization. See 6-2: Unauthorized Access and Unauthorized Use
You might also like to view...
____________________ orientation prints a worksheet on the page sideways.
Fill in the blank(s) with the appropriate word(s).
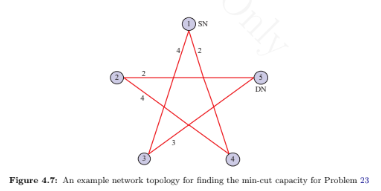
Estimate the time complexities to execute the following routing algorithms: adaptive decen- tralized routing and lookahead routing.
Which of the following risks relates to negative public opinion?
A) Operational risk B) Strategic risk C) Financial risk D) Reputational risk
To describe the purpose of a short or simple table, the ____ element is useful.
A.