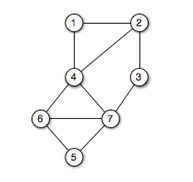
Draw the undirected graph that is represented by the following:
vertices: 1, 2, 3, 4, 5, 6, 7
edges: (1, 2), (1, 4), (2, 3), (2, 4), (3, 7), (4, 7), (4, 6), (5, 6), (5, 7), (6, 7)
You might also like to view...
Which of the following has the worst average-case time bound?
a. binary search b. interpolation search c. sequential search d. two of the above have equivalent average-case bounds e. all of the above have equivalent average-case bounds
Double buffering is a technique that allows an I/O channel and a processor to operate in parallel. On double-buffered input, for example, while a processor consumes one set of data in one buffer, the channel reads the next set of data into the other buffer so that the data will (hopefully) be ready for the processor. Explain in detail how a triple-buffering scheme might operate.
What will be an ideal response?
Describe three ways to
a. Change the size of a window. b. Delete a window.
One tool that provides active intrusion prevention is known as ____.
A. tcpdump B. ICMP C. Vigenère cipher D. LaBrea