Which of the following network devices allows Jane, a security technician, to perform malware inspection?
A. Load balancer
B. VPN concentrator
C. Firewall
D. NIPS
Answer: D. NIPS
You might also like to view...
Describe two innovations introduced by Apple Computer in the late 1970s and early 1980s.
What will be an ideal response?
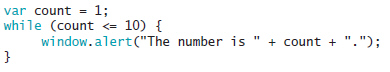 Which of the following statements most accurately describes the code in the accompanying figure?
Which of the following statements most accurately describes the code in the accompanying figure?
A. It will not print "1". B. It will never exit. C. The value of the counter is changed in the loop. D. A do...while loop should be used instead.
Large groups of networked, virtualized servers providing simple interfaces to a vast array of computing resources are referred to as _______________.
Fill in the blank(s) with the appropriate word(s).
Frames in a Flash movie are similar to frames in a motion picture.
Answer the following statement true (T) or false (F)