A VPN concentrator is used for which of the following purposes?
A. MAC filtering
B. Content filtering
C. Secure network access
D. Connectivity troubleshooting
Answer: C. Secure network access
You might also like to view...
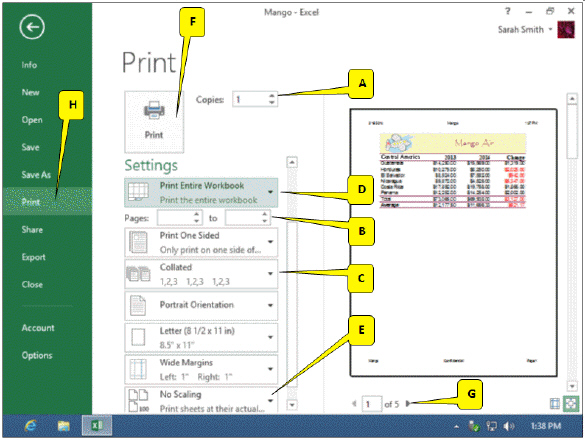 In the accompanying figure, which callout points to the option that allows you to change the default printing option, which prints the active worksheet?
In the accompanying figure, which callout points to the option that allows you to change the default printing option, which prints the active worksheet?
A. A B. B C. C D. D
The text that appears alongside a JCheckBox is referred to as the _____________.
a) JCheckBox value b) JCheckBox name c) JCheckBox text d) JCheckBox data
You can access a subfolder of any folder displayed in the Address Bar by:
A) clicking the arrow to the right of the folder to display the list of subfolders. B) clicking on the forward button on the Address Bar to display a list of subfolders C) right-clicking on the Address Bar to display the list of subfolders. D) double-clicking on the Address Bar to display the list of subfolders.
In the Object Relational Model (ORM) an object-type has a name, attributes, and methods.
a) What is a method? And what is the principal use of methods? b) What kinds of methods are supported by Oracle ORM.